Cybercriminals, fraudsters, and scam artists use a wide variety of tools to turn an illicit profit from their victims. One of the most common tools that corporations face is the dreaded botnet attack.
Estimates cited by Cybercrime Magazine state that “cybercrime will cost the world $6 trillion annually by 2021, up from $3 trillion in 2015.” In short, the use of botnets and other cybercrime tools against your organization isn’t going to go away any time soon. If anything, you can expect to face even more botnet attacks and hacker bots in the near future.
About Bots, Zombie Bots, and Botnets
What Is a Bot?
The term “bot” is shorthand for “robot.” In the context of cybercrime, a bot is an automated software program designed to carry out some specific task.
Bots can be either malevolent or benign depending on what they were made to do. In most cases, they’re made to complete tasks that most people would find too repetitive, boring, and time-consuming to do personally—like answering basic questions, automatically updating data dashboards, or crawling websites on the internet to catalog them for search engines.
Learn More about Bot Programs Now! Download the eBook.
What Is a Zombie Bot?
A zombie bot is a type of malicious bot that turns computers and other devices into drones that a hacker can control remotely. Zombie bots are a key ingredient in creating a botnet and driving large-scale cyberattacks.
What Is a Botnet?
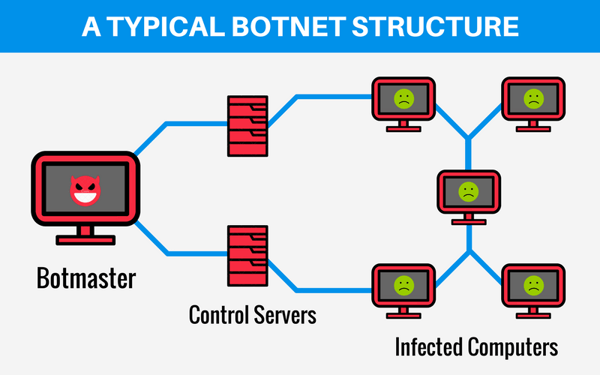
A botnet is a large collection of machines infected with zombie bots that allow hackers to control them remotely. Botnets are often used to perform some kind of illicit task without the device owners’ knowledge.
Once the botnet has grown large enough to meet the hacker’s needs, they can be controlled remotely through so-called command-and-control (C&C) servers. This hacker-side bot management tool often uses standards-based protocols like Internet Relay Chat (IRC) and peer-to-peer (P2P) network to send data to the zombie-infected devices.
How to Create a Botnet
So, how do hackers (sometimes called botmasters or bot herders) create botnets in the first place? Unfortunately, there are many ways in which cybercriminals can create and spread their zombie bots to generate enormous botnets.
Mobile Malware
In this strategy, the fraudster creates a cheap mobile app using a free software development kit (SDK) and uploads it to an online app store. In that mobile app download is a bit of malicious code that creates a zombie bot on any device that downloads the app. This is a common tactic in mobile click fraud schemes.
Social Engineering Attacks
Other hackers might spread zombie bots through malicious links on social media, sketchy websites, and even online ads. An unsuspecting website visitor or social media surfer clicks on the link and suddenly, their device is downloading a zombie bot program (or any of a countless variety of other malware programs).
Fraudsters can spend a lot of time designing enticing online messages to trick unsuspecting victims into clicking on a malicious link. Or, they may simply copy the appearance of an online ad from a legitimate company and create a knockoff that uses a malicious link to install a hacker bot.
Phishing Attacks
Email is the most prevalent source of malware—including the malware used to install zombie bots. According to purplesec.us, “92% of malware is delivered by email.” The use of malware links in emails is one type of phishing technique that some fraudsters and scam artists frequently employ.
Warning signs of a phishing email laden with malware include:
- Urgent language that encourages you to “act now!”
- Use of threats in the email (such as claims that you have overdue payments or your account will be billed if you don’t respond or click on a given link).
- Unsolicited communications from an unknown source.
- Abnormal behavior/language in emails from known sources (phishers often try to imitate people you know so they can trick you).
Types of Botnet Attacks
What can cybercriminals and fraudsters do with the giant botnets they create? The potential uses of compromised, internet-connected devices are nearly endless. Botmasters can use their botnets to conduct a variety of cyberattacks and enable fraud schemes while hiding their tracks.
Some common uses for botnets include:
DDoS Attacks
A distributed denial of service (DDoS) attack is one of the most prevalent uses of a botnet. Here, a botmaster uses their large network of zombie bots to overwhelm a target network or system so that it cannot operate normally. The exact nature of the attack can vary from one DDoS attack to the next.
For example, some DDoS attacks rely on brute force alone, sending countless pings to a network or even a specific device to keep it too busy to process legitimate traffic requests. Others might leverage a specific flaw in a system’s handshake protocols to amplify the delay created if their botnet isn’t especially large.
Whatever the methodology, the botnet keeps the system or network too busy to function normally—impeding the organization’s operations.
Click Fraud
Zombie botnets are often used in click fraud schemes. Here, the horde of zombie bots operates in the background, clicking on ads to drive up clicks for pay-per-click (PPC) campaigns. Advertisers and merchants running PPC campaigns see the clicks they’re getting, think that the affiliate reporting them has helped drive people to click on the ad or website link, and pay the fraudster money.
In recent years, human fraud farms have been used to either supplement or replace click fraud bot schemes. With real humans behind the fraudulent clicks, human fraud farms are often much harder to detect and stop with ad fraud and botnet detection tools.
Discover How Fraudulent Affiliates Use This and Other Fraud Strategies: Download the Whitepaper.
Content Scraping
This is the use of bot programs to steal information from your website. The “scraped” content can then be used in several ways, including:
- Undercutting prices on goods and services;
- Copy content and design elements entirely (often used when creating spoofed websites that imitate a legitimate one); and
- Undermine your website’s SEO by perfectly replicating content on another URL to make it look like duplicate content.
Email Spam
Email phishing attacks often involve sending thousands of messages to people in different companies or departments within a company in the hopes of getting just one person to click on a malicious link. However, a fraudster might not have the email addresses of everyone they want to target.
So, how do they send emails to people they don’t know?
By using bots and botnets to automate the sending of spam and phishing emails to every email address in the contacts list of an infected device. Then, for every recipient that also clicks on the malware link and gets infected with a zombie bot, all of their contacts get sent a message—and so on until the fraudster has built a truly massive network of compromised devices.
Alternatively, fraudsters can use much simpler bots to repeatedly spam large mailing lists of people who have had their contact information collected by third parties without their consent.
Financial Data Breach
Another common use for botnets is to enable breaches of financial institutions. These financial data breaches can result in the compromise of banking access credentials, credit card information, customer contact information, and even personally identifiable information (PII) that can be used in identity theft schemes.
Cybercriminals can either use the stolen data themselves or sell it on the “dark web” for a profit. Some sources indicate that buying credit card details can cost as little as $12-$20 USD.
Real-World Zombie Botnet Attack Example
On October 21, 2016, scores of major websites broke, rendered useless by a DDoS attack powered by a botnet called Mirai. The botnet, largely made up of compromised Internet of Things (IoT) devices, bombarded Dyn, a DNS provider, with malicious traffic, effectively shutting down its services and causing popular sites to go dark.
Securing the IoT ecosystem is proving to be a struggle. On the manufacturers’ side, there aren’t any universal security standards being put in place to regulate the different devices out there and make bot detection easy. Additionally, some manufacturers aren’t releasing critical software updates to outdated devices. In some cases, they orphan them altogether—creating significant security gaps in networks with these devices.
In this instance, the Mirai botnet took advantage of a glaring security flaw that comes shipped with many consumer-ready IoT devices: default user IDs and passwords. As noted by CSO Online: “Mirai took advantage of insecure IoT devices in a simple but clever way. It scanned big blocks of the internet for open Telnet ports, then attempted to log in default passwords. In This way, it was able to amass a botnet army.”
Most people who buy IoT devices don’t change these settings after the initial setup, essentially leaving devices open for hijacking.
The major problem is that IoT devices aren’t going away any time soon. If anything, the use of internet-connected devices is growing. Current projections from Statista forecast the worldwide use of IoT devices to “almost triple from 8.74 billion in 2020 to more than 25.4 billion IoT devices in 2030.”
Finding the Right Botnet Detection
Regardless of how a botnet attack is targeting your organization, the solution may very well be the same. Early botnet detection can prove to be crucial for effectively responding to (and stopping) the attack.
A bot that attacks your website isn’t typically going to behave exactly like a normal human visitor. For example, it will often fail to log on to various services, quickly load up items into then promptly abandon carts, exhibit irregular viewing behavior (being on-page for less than a second), and do weird things to your online forms. Additionally, botnet traffic tends to hit all at once (though more sophisticated fraudsters may stagger their zombie bots’ efforts).
However, these warning signs aren’t always easy to spot manually—and manual checks take precious time to complete. To protect yourself from botnet attacks, you need to know who is visiting your site in real-time. You need to analyze where incoming traffic is coming from and what it is doing. You need to be able to identify bots before the issue gets out of hand. You will require an ad fraud solution.
A professional, high-quality ad fraud solution such as Anura, will monitor your traffic constantly to determine which visitors are real and which ones aren’t. Once identified, you’ll get a notification of the invalid traffic that came from bots (and other sources of fraud)—complete with a report of the data showing why the activity was tagged as fraud. This allows you to clear out the bad while keeping the good.
Your business is free to go back to doing what you do best, without having to worry about where the next attack is coming from. In the modern age, no one is too big or too small to be targeted by fraudsters taking the easy road to riches, but you can control how hard it is to hit you. Don’t be an easy target, demand a free trial today.